
Psst!…..Forward this article to your accountants, legal counsel, or anyone else on your team working with W-2 data.
Late last week, we (along with many other security firms) identified a simple and recognizable phishing scam popping again on accountants and other folks working with W-2 forms.
The Problem With Phishing Emails This Year?
The scam is more complex and may confuse unsuspecting recipients. The most recent W-2 scam is more complicated than previous scams. After a first request for W-2 information (which contain sensitive information, including Social Security Numbers!), the scammer sends another spoofed email from a separate account following up on the first email—often confusing staff into divulging the requested documents.
While the IRS warns that this scam is targeted at individual consumers, security experts warn that scammer’s real target (and payload) are from businesses like yours!
What Should Your Team Be Looking For?
The W-2 scam often is spoofed to come from the CEO or CFO of the company and is directed to staff in HR, payroll and an executive assistant. In fact, some cyber criminals are so good, they research everyone in your company—either on your website, through LinkedIn or other public databases—to identify the targets of the attack. Their up-front investment of 20 minutes of research often pays off big time.
These emails often are asking for urgent attention. The CEO or CFO needs the W-2 information ASAP. Urgency in the message helps create emotion within recipients to act know (instead of thinking first). The criminals are asking for W-2s specifically in the emails because the information enclosed on a W-2 form provides sufficient information—name, address, Social Security Number and income information—to not only fraudulently file false returns and reap big refunds, but to pursue further exploits via full on identity theft.
Here is an example of an email. Let’s say your CEO is named Heather Smith and Steve Adams is your business’ payroll officer:
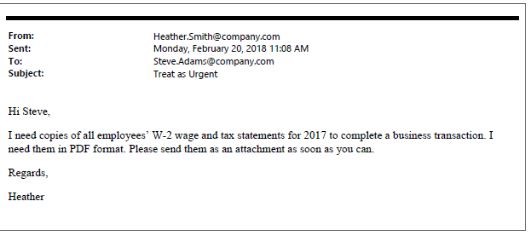
The email seems legitimate. It is timely in that W-2s are being processed right now. The email address seems correct. Some variations may not be sophisticated to completely spoof the sender address (i.e., the address is likely not quite right—this is one tell-tailed sign of a phishing attack). But in some instances, hackers can completely mask emails to appear as if they were sent from the correct address. In this case, we have a sophisticated attack on our hands!
Having heeded advice on how to detect phishing scams (but see our page on avoiding scams here), many users may be very suspicious of such a strange request from a first email.
The Problem With the Most Recent W-2 Phishing Scams?
Scammers aren’t giving up with just one try! They’re actually upping the ante to a secondary email that lets the user (your accountant for instance) know that they know about the first email and—in some cases—to inform the employee that that first email was in fact a scam. The second email instructs the user to send the W-2 information to a different email address (often a personal address), to something like CEO@gmail.com.
Because of their initial success, we expect the W-2 scam to be widespread for the rest of tax season. According to the IRS, scammers had over 200% gain in success rates in 2017, encouraging many more criminals to implement similar attacks in 2018. Security experts have also seen exponential growth in attacks over the past 5 years with no sign of stopping in the near future. Plus, the low cost to spoof an email, do a little background research on your business and target your employees is relatively low cost, allowing for criminals to reap big payoffs with very low upfront investment.
Bottom line: the cards all show increased W-2 scams and other sophisticated phishing scams for 2018. Scams will be written in better English and will target specific roles in your organization. Without proper training and preparedness, you may lose big bucks if you’re not careful!
What Should You Do to Make Sure You’re Protecting Your Users?
Re-educate all of your team — it’s so easy to forget the basics of how to identify a phishing scam, but it’s also easy to overlook good security hygiene at your workplace. If you are a Dynamic Edge client, you can request personalized security training for your office. We also encourage attendance in our cybersecurity webinars, which will count towards your staff’s annual HIPAA training if you work in healthcare and need to stay compliant with HIPAA standards.
Question before your respond — make sure you send the message throughout your office that you’re never going to ask for sensitive information via email. Create a culture that questions and confirms out of the ordinary requests (for information or money) rather than simply following directives.
Never click on links in emails — one of the fastest ways into your network is by getting users to click on spoofed links to malicious websites. Instead of directly clicking on links in emails, we recommend you copying the link address and pasting it in your browser to be safe you aren’t redirected to the wrong place.
Get verbal confirmation — if you or your staff suspects that a request is funny, have them get verbal confirmation before acting. This could save you big time when it comes to divulging sensitive data or making big money transfers.
Bottom Line? ALWAYS DOUBLE CHECK.
If something doesn’t seem or feel right, it likely isn’t. And if the request was legitimate, the requester probably will appreciate that you double check with them before risking sending it to a scammer.
Is your team prepared for the next big scams? Is your network vulnerable to the latest ransomware attacks? Contact us today for a FREE ransomware and network security assessment. You can report a W-2 phishing email directly to the IRS by following the steps on the official IRS website.

